111 billion lines of new software codes are produced on a yearly basis. This gives cybercriminals a MASSIVE amount of vulnerabilities to exploit.
NetworkWorld claims that 111 billion lines of new software codes are produced on a yearly basis. You can imagine the amount of vulnerabilities out there waiting to be exploited. To make matters worse, NETSCOUT found that IoT (Internet of Things) devices are typically attacked within five short minutes of connecting to the Internet. How many employee- or company-owned devices are connecting to your network day after day? Can you really trust that each individual using your network knows what they’re doing in regards to cybercrime?
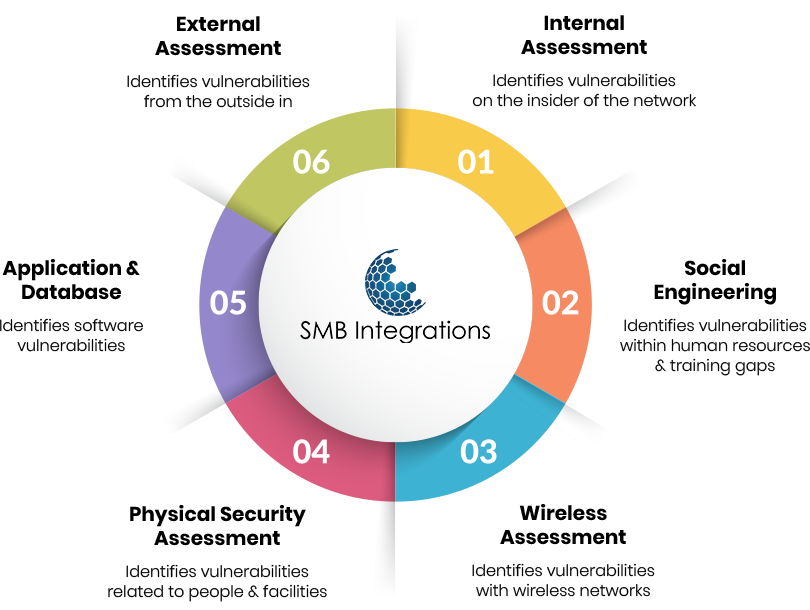
Why Do You Need a Network & Security Assessment?
Nothing impacts a company’s reputation quite like a security breach. When it comes to cybersecurity, all individuals within the company must be involved and aware of the risks — from the board members to the CEO to the employees. Every company, regardless of type or size, holds some sort of valuable intellectual property and trade secrets. If this data hasn’t been compromised yet, there will likely be an attempt made in the near future. This is simply how the threat landscape works nowadays.
SMB Integrations provides network and security assessments wherein we test your security measures and/or policies and procedures. This includes:
- Creating a detailed database of all technology assets
- Analyzing login history to spot any sort of unusual activity
- Reviewing any existing security policies and procedures
- Searching for confidential information in areas it’s not authorized to be
- Detecting any vulnerabilities found on the network or connected devices
- Delivering a comprehensive report of your current risk level and recommendations
We do this because we know undergoing regular, periodic security assessments is essential for all businesses — allowing them to have peace of mind knowing:
- Any cloud-based environments are secure in terms of cloud visibility and control tools to ensure all data at rest and in transit cannot be accessed by unauthorized users. Although most cloud providers follow standard protocol in terms of security, most cloud security breaches result from human error and/or oversight.
- Any applicable industry-specific compliance mandates are met including all physical and technological security requirements. This includes those in relation to HIPAA, GDPR, PCI DSS, FISMA, and others, many of which actually require you to pass a third-party audit.
- Any undetected security breaches are found as many companies are unaware of a security breach on the network until confidential data gets leaked or the attacker demands a ransom. This helps to minimize the cost and/or reputational damage associated with a breach.
What About Dark Web Monitoring?
The dark web is essentially a misunderstood network that contains a range of criminal activities. It’s commonly referred to as the back web. Similar to the internet, the dark web is a network of communication tools, websites, and forums. Traditional browsers can’t access the dark web without the proper security plugins. Although the dark web does serve some reputable purposes, it’s commonly used by cybercriminals due to its anonymous nature. A wide range of confidential information can be found there:
- Leaked data
- Financial information
- Trademark and copyright infringements
- And more
Naturally, the first step to protect your sensitive data from ending up on the dark web is having the right security solutions in place. This includes firewalls, antivirus software, access control, web content filtering, and more. SMB Integrations provides comprehensive cybersecurity solutions that are multilayered to protect all areas of your environment. We also provide dark web monitoring wherein sophisticated dark web intelligence is combined with search capabilities to identify and monitor data to prevent loss or theft.
This allows us to determine the exact moment your data ends up on the dark web, in the event an attacker manages to get through our comprehensive, multilayered cybersecurity approach, with alerts sent to us immediately. This, in turn, gives you the ability to act fast.
Invest in a network and security assessment before it’s too late. Call (832) 617-0033 or email us at [email protected].